DVWA Weak Session IDs Low Sec - Red Team
In today’s short Red Team only post we will look at Weak Session IDs on Low Security. It’s a swift read and simple (Vulnerable) tracking system.
Prerequisites
If you don’t currently have a Damn Vulnerable Web Application (DVWA) instance you can follow along at home with a simple git clone & vagrant up if your host system meets the minimum specs.
Red team only deploys Opnsense, DVWA, and Kali.
Weak Session IDs
This one on low sec is trivial; it just sets the dvwaSession cookie to +1 each time. So the first time you generate it you’ll get dvwaSession=1 then 2,3 and so on.
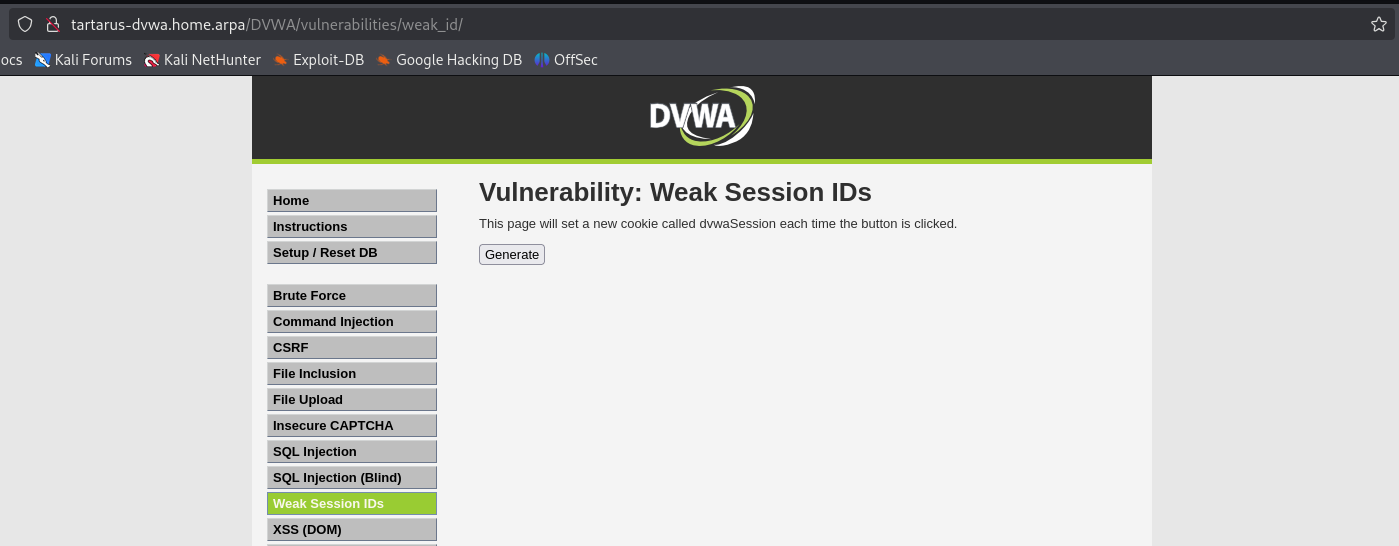 Example weak session ids main page
Example weak session ids main page
Now to have a look at the cookies, start by inspecting the page before generating the cookie to see all network activity.
If this was a real session ID it would be a breeze to impersonate it.
Credits
Image thanks to Nasa AS11-44-6549
Icon thanks to Gate icons created by juicy_fish - Flaticon