DVWA Tartarus Prerequisites - Red Team
Note
This will only bring up Red Team related guests, if you want to participate in the Blue Team / SIEM aspects you’ll need the start the Blue Team Tartarus Lab, guide located here.
Video
Conventions
Commands for you to execute are encapsulated in code blocks like this
1
this
The data returned from a command will be represented pictorially like this:
Info looks like this
Tips look like this
Warnings look like this
Danger looks like this
Requirements
To follow along at home for the Red Team perspective of the DVWA you will need the following:
- Vagrant
- VirtualBox
- Git
- Time
- Windows or Linux host OS
- Some terminal or Powershell awareness
Your host will need the following resources:
Red team default
RAM: 11 GB
CPU: 7 vCores (4 physical cores)
Red team min
RAM: 6 GB
CPU: 4 vCores
Installation
The Tartarus Lab located here.
The Nuclei templates are located in the nuclei-templates directory.
Have Vagrant, VirtualBox and Git installed.
In Powershell or the terminal (sh, bash, zsh, fish, etc.):
- Linux
1 2
git clone https://github.com/ScioShield/Tartarus.git cd Tartarus - Windows
1 2
git clone https://github.com/ScioShield/Tartarus.git cd Tartarus
Once the Tartarus Lab has been downloaded you can now bring up the machines with:
- Linux
1
export VAGRANT_VAGRANTFILE=Vagrantfile.red; vagrant up opnsense
Then run:
1
vagrant up opnsense dvwa kali
- Windows
1
$env:VAGRANT_VAGRANTFILE = "Vagrantfile.red"; vagrant up opnsense
Then run:
1
vagrant up opnsense dvwa kali
As documented here in the readme, there is the min option to deploy with only 6 GB RAM and 4 vCores.
Expected terminal results (trimmed for convenience):
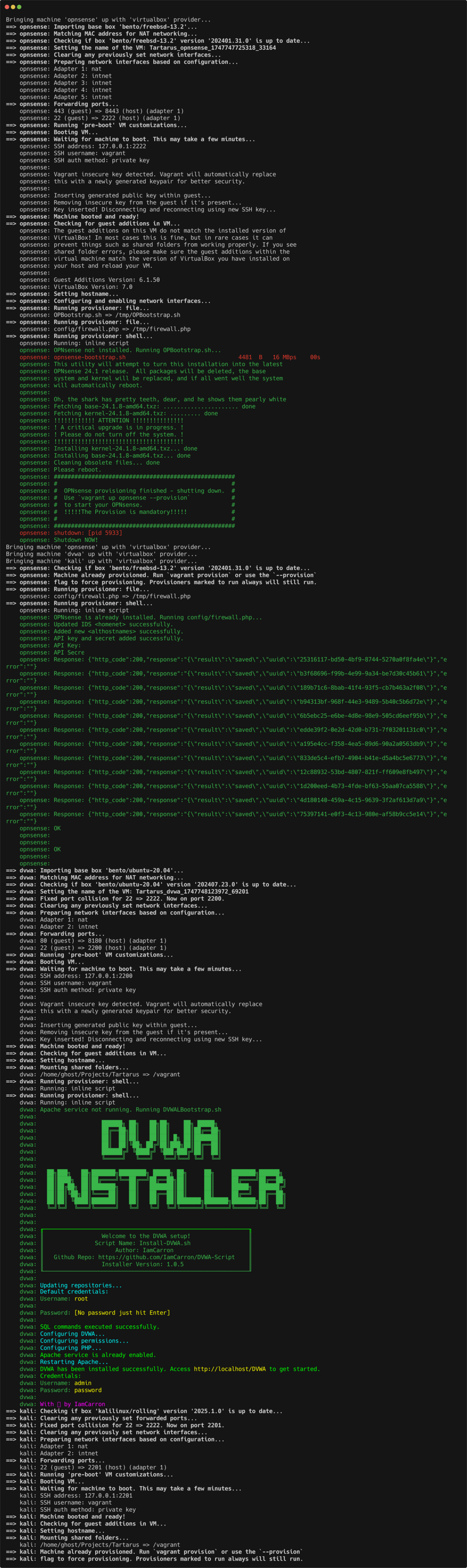 Output of bringing the hosts up with vagrant on Linux
Output of bringing the hosts up with vagrant on Linux
Architecture
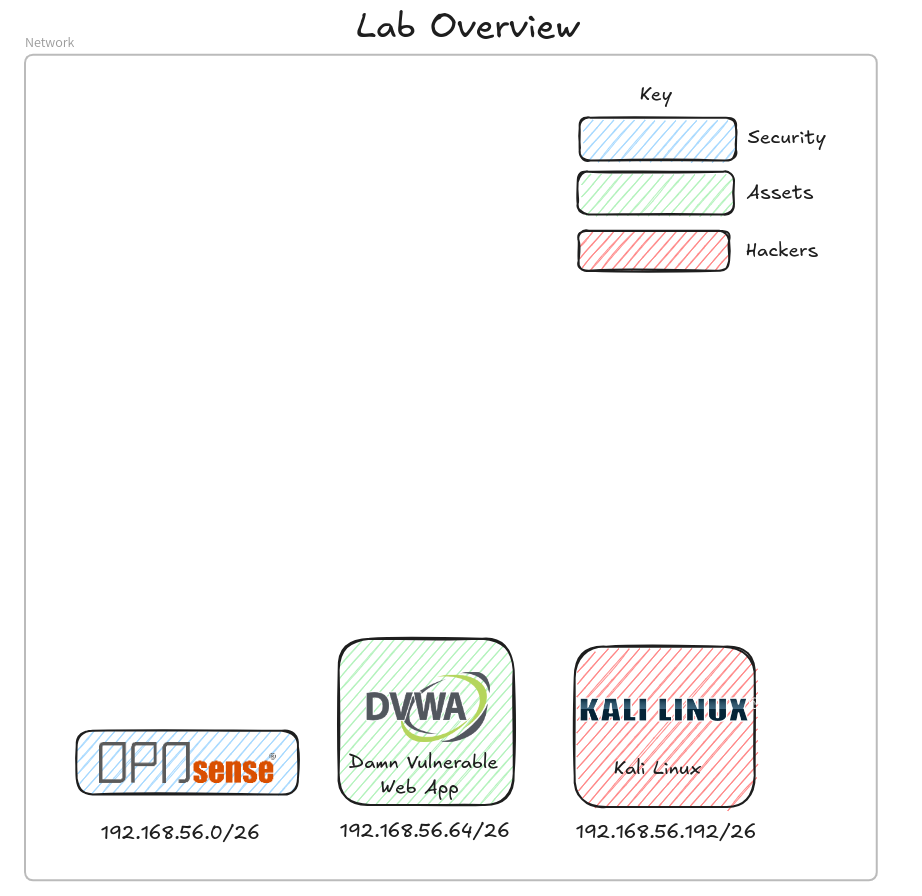
For this lab we only have Red team related guests, Opnsense, DVWA, and Kali. The Opnsense node is required to facilitate network connectivity between guests.
Opnsense
You can log into the Opnsense firewall by going to https://tartarus-opnsense.home.arpa:8443/ once you’ve updated your hosts host file to point tartarus-opnsense.home.arpa to 127.0.0.1.
Username: root
Password: opnsense
To maintain network segregation we use an Opnsense firewall. The firewall acts as a stateful firewall, DNS, DHCP, and NTP server. We use a class C network the “192.168.56/24” that we subdivide into 4 /26 networks, so with the WAN network we have LAN (or Security in the above diagram), Assets, Targets, and Hackers.
mindmap
root((Firewall Rules))
LAN
Allow
ANY
ANY
ANY
WAN
Allow
TCP
HTTPS
self
SSH
self
Assets
Allow
UDP
NTP
self
DNS
self
TCP
Elasticsearch
LAN
Web Traffic
ANY
Block
ANY
ANY
RFC1918
Targets
Allow
TCP
Elasticsearch
LAN
Block
ANY
ANY
RFC1918
Hackers
Allow
UDP
DNS
self
NTP
self
TCP
Web Traffic
ANY
SSH
Assets
A mind map representation of the firewall rules.
Damn Vulnerable Web Application
The many blog posts on the DVWA makes it a prime target to demonstrate the Tartarus playground. All the supporting infrastructure allows for a near plug-and-play solution, the only modifications needed are to add the Apache Web server integration, install the Elastic Agent, and install the DVWA on a Debian based distro in this case Ubuntu.
 Example DVWA login page from Kali.
Example DVWA login page from Kali.
Kali
The only guest in the Hackers network, this guest is the beach head into the rest of the network. You can customize the base image to your harts content, or just destroy it and start fresh every time.
username: vagrant
password: vagrant